Runtime Application Self-Protection (RASP) is a powerful ally in the continuous fight to protect programs from exploitation and compromise in the field of cybersecurity, where dangers are around every digital corner. RASP provides unmatched protection via real-time threat detection and mitigation, strengthening businesses’ security posture and enabling them to confidently negotiate the digital world. The article will go into the main rasp security aspects in this thorough guide, giving companies the information and tactics they need to fully use this cutting-edge protection mechanism.
Recognizing RASP Security
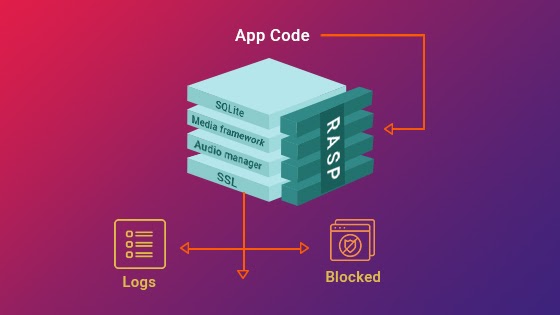
Fundamental to RASP security is the idea of integrating security measures into the application stack such that runtime proactive threat detection and mitigation is possible. By operating within the program itself, RASP provides fine-grained visibility and control over its behavior and interactions, unlike conventional security solutions that depend on perimeter defenses or outside monitoring tools. Through real-time monitoring of the application’s runtime environment and analysis of its execution routes, RASP is able to detect and handle dubious behaviors like code injection, attempts at illegal access, and data exfiltration.
Principal Things to Think About in RASP Security
Organizations need to consider many important factors in order to optimize RASP security’s efficacy and guarantee thorough defense against changing threats:
Methodology of Deployment
Success of RASP implementation depends on selecting the appropriate deployment architecture. When choosing a RASP deployment approach, organizations must consider things like scalability, performance effect, and compatibility with current infrastructure. Whether implemented as a cloud-based service or as an agent within the application runtime environment, the selected architecture should provide strong threat protection while integrating smoothly with the current systems and procedures of the company.
Detailled Policy Administration
The capacity to create and maintain detailed security rules suited to the particular needs of the application and its surroundings is essential to RASP security. Policies should be configurable by organizations according to things like the kind of application, the business logic, the user roles, and the needs for regulatory compliance. By enabling companies to balance security and usability, granular policy management guarantees the protection of important assets without compromising the application’s performance or usefulness.
Integration of Threat Intelligence
Including threat information feeds into the RASP system improves its real-time threat detection and response capabilities. Organizations may strengthen their defenses with current knowledge about known attack vectors, malware signatures, and malevolent IP addresses by using threat intelligence data from reliable sources such industry consortiums, cybersecurity companies, and government agencies. Because of its proactive approach to threat identification, RASP is able to keep ahead of changing threats and modify its defensive plans as needed.
All-Inclusive Attack Protection
RASP security need to provide thorough defense against a large number of attack paths, flaws, and methods of exploitation. From cross-site scripting (XSS) and injection assaults to attempts at illegal access and data modification, RASP ought to be able to identify and counteract a wide range of threats directed at the application. To be sure important vulnerabilities are sufficiently protected against, organizations should assess the depth and breadth of attack coverage provided by RASP solutions.
Compatibility with DevSecOps Procedures
RASP security integration with DevSecOps procedures makes security controls easy to include into the application development lifecycle. Organizations may find and fix security problems early in the development process by integrating RASP into automated build and deployment pipelines, therefore lowering the possibility that vulnerabilities will find their way into production systems. Security by design, or giving security issues top priority at every phase of the development lifecycle, is promoted by integration with DevSecOps procedures.
Constant Observation and Reporting
Strong monitoring and reporting features should be included into RASP security to let businesses monitor and examine security occurrences instantly. RASP should provide thorough insight into the security posture of the application, from warning administrators of dangers found to producing thorough reporting on security events and policy infractions. Organizations that continuously monitor and report are better able to predict security problems, reduce risks, and show that they are in compliance with regulations.
Performance and Scalability
In dynamic, busy settings, scalability and performance are critical factors to take into account while installing RASP. To be sure RASP systems can handle changes in application traffic and use without sacrificing availability or performance, organizations should assess their scalability. To preserve the best possible user experience and responsiveness, RASP should also have as little of an effect on the application runtime environment’s performance.
Particularization and Extension:
Customization and extension of RASP solutions are necessary to satisfy the particular security needs of various applications and settings. To suit their particular risk tolerance and compliance needs, organizations should be able to tailor security policies, procedures, and thresholds. RASP should also provide integration with current security frameworks and tools, therefore enabling businesses to take use of their security infrastructure and technology investments.
Regulatory Compliant and Auditable:
Organizations using RASP security have to be able to meet and stay in compliance with industry norms and regulations. Through the provision of audit trails, logs, and reports proving compliance with security policies and regulatory requirements, RASP helps companies show stakeholders and regulatory agencies that they have done their due diligence. Implementing the security controls and controls monitoring procedures needed for compliance is made easier by integration with compliance frameworks and standards.
Instructional & Training:
Putting money into training and education for staff members in charge of running and monitoring RASP security improves its efficiency and guarantees best use of its potentialities. Complete training courses on RASP deployment, setup, operation, and maintenance should be offered by organizations to security teams, developers, and administrators. Furthermore, constant training on new risks, best practices, and application scenarios enables staff members to make wise judgments and optimize the benefits of RASP security in safeguarding important assets.
Conclusion
RASP security provides a proactive and successful defensive system to protect applications from many different dangers and weaknesses. The runtime application self-protection offers complete coverage of attacks, extensive policy administration, and real-time threat detection and mitigation by integrating security controls directly into the application stack. But a successful RASP deployment needs to take deployment architecture, policy management, threat intelligence integration, attack coverage, DevSecOps integration, monitoring and reporting, scalability and performance, customisation and extensibility, regulatory compliance, and training and education into serious account. Organizations may fully use RASP security to safeguard their apps and data from exploitation and compromise by taking care of these important issues, strengthening their defenses in a digital environment that is becoming more and more hostile.